

Application Request Routing (ARR) is an optional feature that is available for Microsoft Internet Information Services (IIS). ARR directs requests to other servers, much like a proxy server.
The IIS web server processes cookies differently with ARR. This configuration affects how CA SiteMinder® cookies are processed with FCC authentication schemes.
This scenario describes the additional configuration settings that <stmdnr> agents require in any of the following situations:
The following illustration shows how a system administrator configures CA SiteMinder® for ARR with FCC:

To configure your CA SiteMinder® agents to use ARR and FCCs together, follow these steps:
Verify Prerequisites
The following illustration describes the components and prerequisites of your environment:
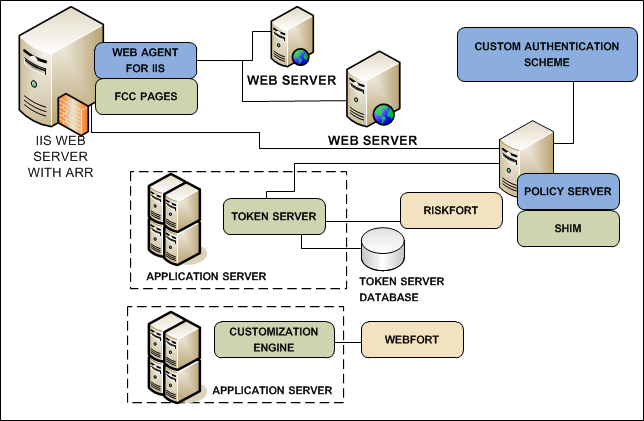
Verify that your CA SiteMinder® and CA DataMinder environments meet the following requirements:
Set the Parameter Values for ARR and FCC
To set the parameter values for ARR and FCC, follow these steps:
The CA SiteMinder® Forms Credential Collector (FCC) is designed to enable CA Services to trigger custom authentication schemes securely. As such, the FCC can authenticate users against any authentication scheme. However, the FCC does not authenticate against Windows authentication schemes by default. This behavior prevents an attacker from exploiting the FCC to generate a CA SiteMinder® session for any valid Windows user in certain configurations.
If your environment requires the FCC to authenticate against the Windows authentication scheme, you can enable it by specifying the EnableFCCWindowsAuth agent configuration parameter. However, before you enable FCC support for Windows authentication, review the risks of doing so and be aware of configurations that expose the vulnerability.

Risks of Enabling the FCC to Allow Windows Authentication
By default, the FCC does not authenticate against Windows authentication schemes. You can enable the FCC to allow Windows authentication. However, doing so exposes a vulnerability whereby an attacker could use an FCC to generate a CA SiteMinder® session for any valid Windows user in certain configurations.
The vulnerability is present in configurations in which the same CA SiteMinder® Agent name or Agent group name is used in both an HTML Forms-protected realm and a Windows-protected realm. For example, a configuration in which a single Web Agent is configured to protect different realms that are configured with HTML Forms and Windows authentication.
Consider the following example scenario:
The attack occurs as follows:
The result is a CA SiteMinder® session returned to the user which enables single sign-on for all following requests where the new session is considered valid. The attacker is now impersonating the user whose Windows username was submitted to the FCC.
Configure the FCC to Allow Windows Authentication
You configure the FCC to allow Windows authentication by specifying the following agent configuration parameter:
Specifies whether an agent, acting as an FCC, can authenticate users against resources that the CA SiteMinder® Windows authentication scheme protects.
This parameter uses the following values:
Important! When this parameter is set to Yes, an attacker can potentially exploit the FCC to impersonate Windows users without providing required credentials.
Default: No
|
Copyright © 2013 CA.
All rights reserved.
|
|